Mobile App Security Best Practices for a Hack-Proof App
The role of mobile in our lives cannot be denied. For the majority of individuals mobile applications have become the focal point of technology usage. It encompasses a broad spectrum of personal and confidential user information, encompassing medical records and financial data. Given the growing dependence on mobile applications, the importance of strong mobile app security has reached a critical level.
Security breaches can lead to the exposure of data, financial setbacks, and harm to a company’s image. To ensure a hack-proof app, developers and iOS app development company must follow best practices in mobile app security.
Why We Need Mobile App Security: Identifying Threats and Their Solutions
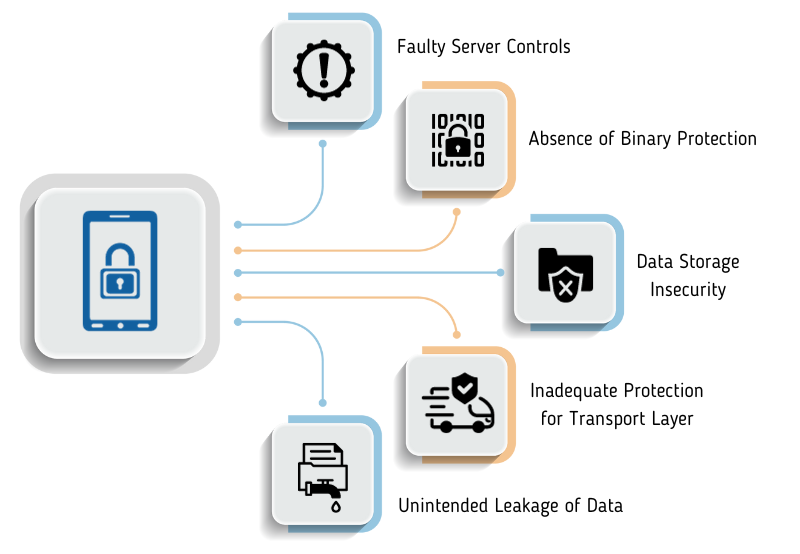
As the world of technology is advancing at a breath-neck pace so are the threats. While these threats are inherently malicious, they can frequently be alleviated by employing simple security measures. Within this blog post, we shall delve into the security challenges confronted by mobile applications and present remedies to tackle them.
Faulty Server Controls:
Communication between mobile apps and users often occurs through servers, which makes these servers prime targets for hackers.
The vulnerability of a server can arise when developers overlook necessary server-side security measures. This can be due to a lack of knowledge about mobile application security, budget constraints, or vulnerabilities stemming from cross-platform development.
Solution: A crucial step in safeguarding servers is to scan apps using automated security scanners. These scanners can identify common issues and bugs, making them easier to resolve.
Absence of Binary Protection:
Failure to protect binary code in a mobile app can allow hackers to reverse-engineer the code, introduce malware, or redistribute pirated versions of the app, leading to data theft and damage to a brand’s image.
Solution: Deploy binary hardening procedures to analyze and modify binary files, protecting them against common mobile app security threats. Ensure security coding detects jailbreaks, checksum controls, debugger detection, and certificate pinning.
Data Storage Insecurity:
Insecure data storage practices can expose internal data, making it accessible to malicious actors. This can lead to crimes such as identity theft or violations of external policies like PCI.
Solution: Implement an additional encryption layer over the device’s base-level encryption to enhance data security.
Inadequate Protection for Transport Layer:
The transport layer, responsible for data transfer between clients and servers, can be vulnerable to hackers if proper mobile app security standards are not in place. This can result in identity theft and fraud.
Solution: Strengthen the transport layer’s security by incorporating SSL pinning in iOS and Android apps. Use industry-standard cipher suites, avoid exposing user session IDs due to mixed SSL sessions, alert users in case of invalid certificates, and use SSL versions for third-party analytics.
Unintended Leakage of Data:
Unintended data leakage occurs when sensitive mobile app data is stored in vulnerable locations on the device, making it susceptible to breaches and unauthorized access.
Solution: Monitor common data leakage points, including logging, app background processes, caching, browser cookie objects, and HTML5 data storage.
Apart from these five prevalent mobile app security threats and their respective remedies, there are additional hurdles when it comes to constructing secure mobile applications. These include:
- Absence of Multi-Factor Authentication: Implementing multi-factor authentication adds layers of security to the app, reducing the risk of unauthorized access.
- Inadequate Encryption: Proper encryption is crucial to protect against code theft, intellectual property theft, privacy violations, and more.
- Malicious Code Injection: User-generated content, such as forms, can be exploited to inject malicious code, compromising the app’s security.
- Reverse Engineering: This can expose an app’s backend functionality, encryption algorithms, and source code, posing a significant security risk.
- Insecure Data Storage: Data stored in various places within an app, such as cookies, binary data stores, or SQL databases, can be vulnerable to hackers if not properly secured.
Developers must grasp threats and security practices for Android and iOS apps. By implementing robust security measures and staying informed about emerging threats, developers can build safer and more secure mobile applications.
Ensuring Secure Android Apps: Best Practices to Follow
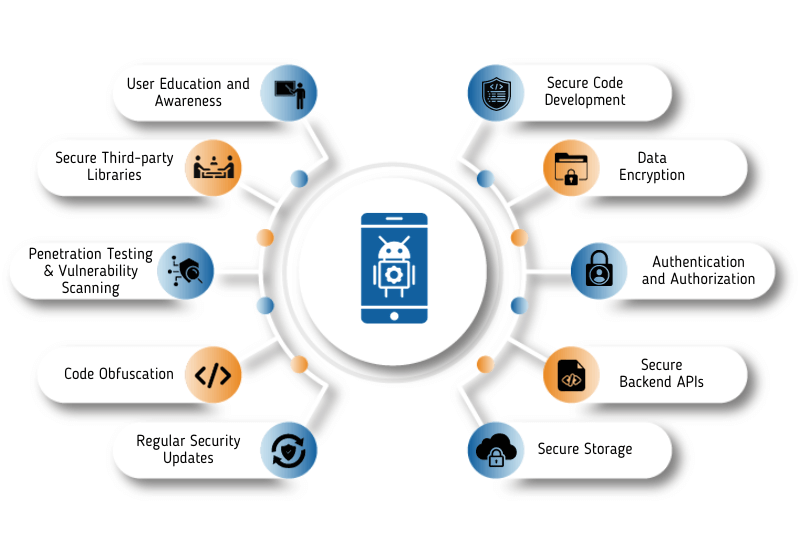
Secure Code Development:
The foundation of mobile app security begins with secure code development practices. Developers should follow industry-standard coding guidelines and utilize secure coding frameworks.
Regular code reviews and testing for vulnerabilities are crucial. Tools like static code analysis and dynamic analysis can help identify and mitigate security flaws early in the development process.
Data Encryption:
Data encryption constitutes a fundamental component of mobile app security. Developers must guarantee the encryption of sensitive information, such as user credentials and payment details, both during transmission and while stored.
It is imperative to employ robust encryption algorithms like AES. Furthermore, developers should establish secure key management protocols to protect encryption keys.
Authentication and Authorization:
Establishing resilient authentication and authorization mechanisms is essential to safeguard user data and thwart any unauthorized access to the application.
Enforcing multi-factor authentication and stringent password policies is imperative. Additionally, role-based access control can be instrumental in guaranteeing that solely authorized users gain access to specific app functionalities and data.
Secure Backend APIs:
Many mobile apps rely on backend APIs to fetch and send data. It’s essential to secure these APIs to prevent data breaches.
Implementing API authentication and authorization, rate limiting, and input validation are essential measures. API endpoints should be properly documented, and only necessary data should be exposed.
Secure Storage:
Sensitive data stored on the device, such as cached user credentials or offline data, must be stored securely.
Cross-platform Mobile App Development Company should utilize secure storage mechanisms provided by the platform, such as the Keychain on iOS and Android Keystore on Android. Data should be encrypted, and access should be limited to authorized app components.
Regular Security Updates:
Security threats evolve constantly, and vulnerabilities can emerge over time. Therefore, it’s crucial to keep the app up-to-date with security patches and updates.
iOS app development agency and cross-platform mobile app development company must have a robust update mechanism in place to ensure users are using the latest, most secure version of the app.
Code Obfuscation:
Code obfuscation is a technique that makes it difficult for attackers to reverse-engineer an app’s code. Obfuscating the code can help protect intellectual property and sensitive algorithms.
Developers should use obfuscation tools to make it challenging for attackers to understand the inner workings of the app.
Penetration Testing and Vulnerability Scanning:
Penetration testing and vulnerability scanning are essential for identifying and addressing security weaknesses. These processes involve simulating real-world attacks on the app to discover vulnerabilities that could be exploited by hackers. Regular testing and scanning should be conducted throughout the app’s lifecycle.
Secure Third-party Libraries:
Mobile apps often rely on third-party libraries and SDKs to enhance functionality. However, these libraries can introduce vulnerabilities if not properly vetted.
Developers should regularly review and update third-party components, ensuring that they are free from known security flaws.
User Education and Awareness:
While most of the responsibility for mobile app security falls on developers and organizations, users also play a crucial role.
Developers should educate users about security best practices, such as setting strong passwords, enabling MFA, and being cautious about downloading apps from un-trusted sources.
Conclusion:
In an era where mobile applications have seamlessly integrated into our daily routines, the imperative of safeguarding these apps cannot be overstated.
The security of mobile apps is a collective responsibility, shared between iOS app development entities and the user community.
By steadfastly following established guidelines, including secure code development, data protection through encryption, robust authentication procedures, and a commitment to regular security updates, developers can substantially reduce the vulnerability to security breaches.
Furthermore, cross-platform mobile app development firms also play a noteworthy role in upholding stringent security standards for mobile apps.
In addition, it is paramount to institute ongoing surveillance and rigorous testing to maintain an advantage over evolving threats.
In a landscape where cyber adversaries perpetually seek weaknesses, adopting a proactive stance toward mobile app security emerges as indispensable in the creation of applications that remain impervious to illicit intrusion and, in turn, instill user confidence.



